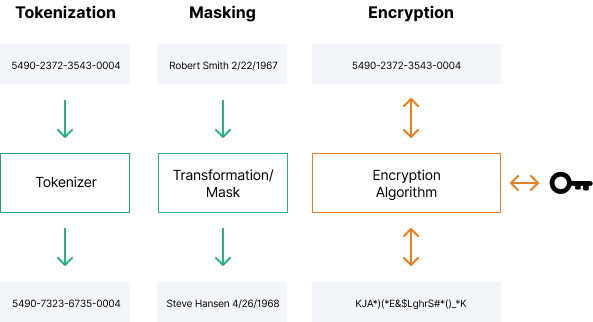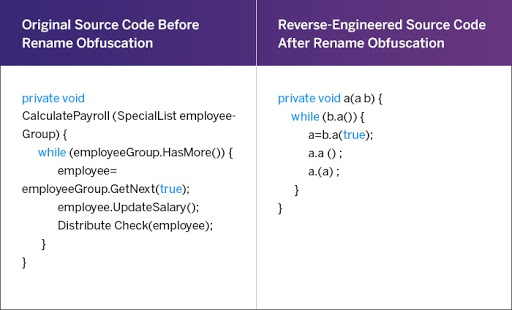
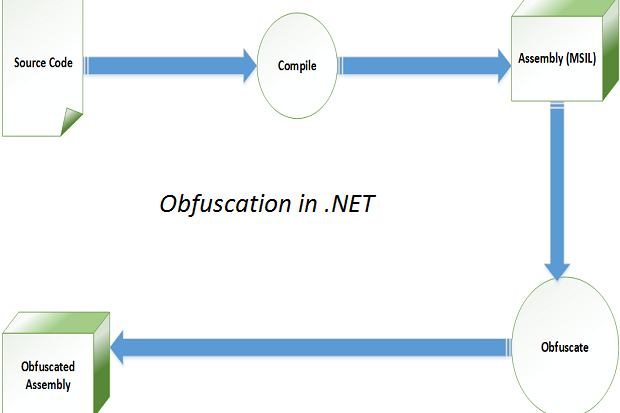
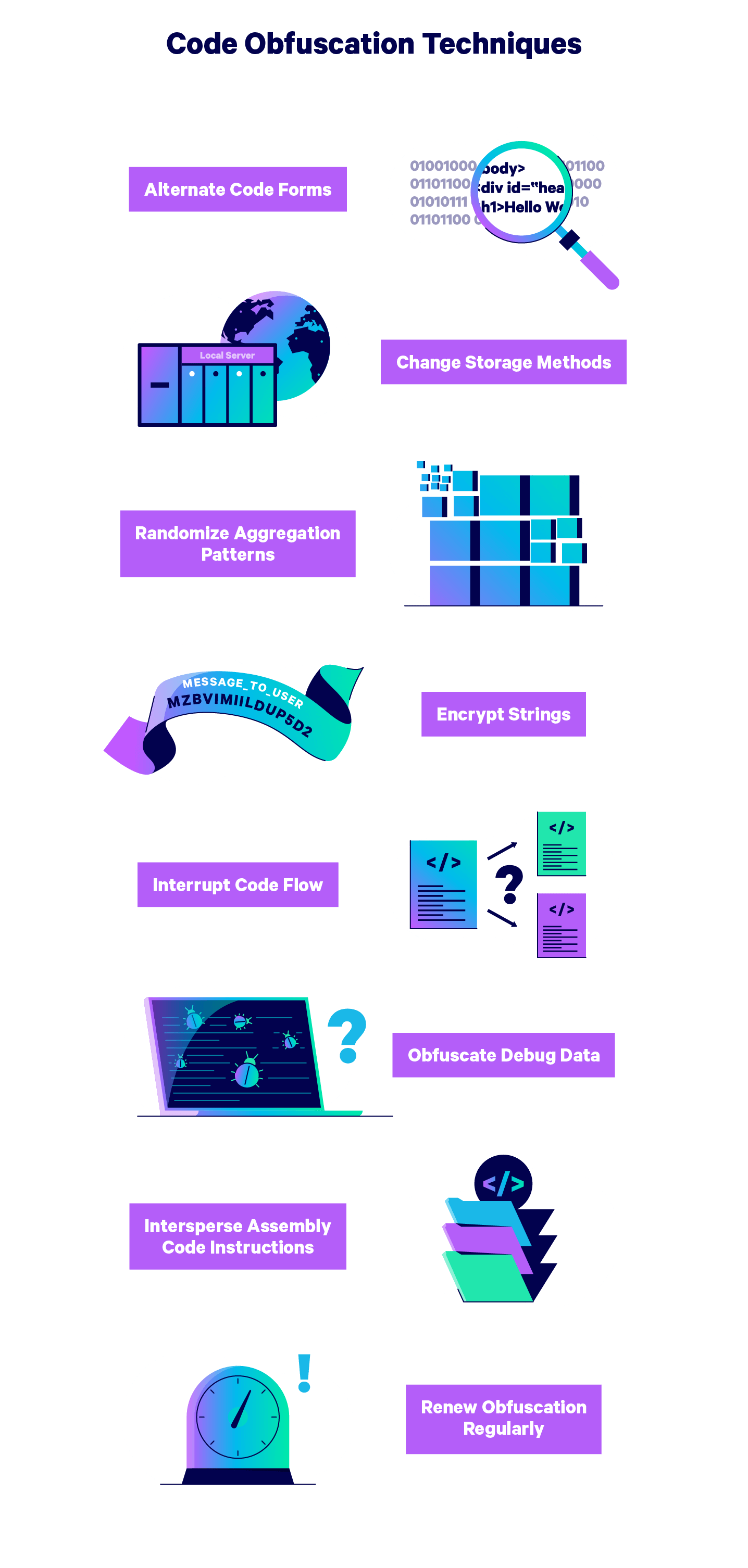
Layered obfuscation: a taxonomy of software obfuscation techniques for layered security | Cybersecurity | Full Text

Obfuscation Techniques Ppt Powerpoint Presentation Styles Ideas Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates












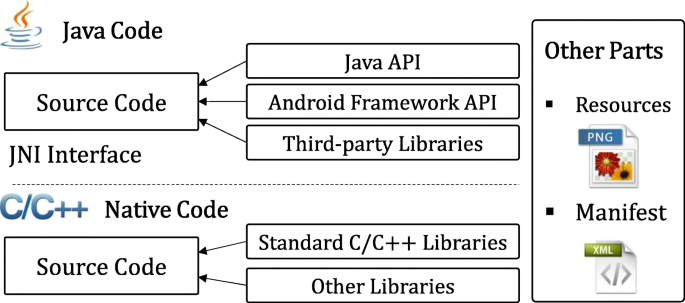
![On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ] On the evaluation of android malware detectors against code-obfuscation techniques [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2022/cs-1002/1/fig-3-full.png)